Cybersecurity Solutions from BPM
Unlike other security solutions that are expensive, rigid, and one-size-fits-all, BPM offers a range of options based on your particular needs
- BPM.NCRYPT is Flexible: It can integrate with your existing security systems. Can be customized to the unique requirements of the project
- BPM.NCRYPT is Scalable: we don’t require a separate HSM for each of our automated systems; One HSM (or secure server) can support several BPM high-speed programming systems
- BPM.NCRYPT is Affordable: BPM does not charge per device and all of our APS are enabled to support encryption; you have an initial investment with no usage fees
Flexible, Scalable, Affordable
BPM.NCRYPT can utilize your existing HSM, secure server, or many other networked and offline data sources. BPM Microsystems can also provide a turn-key package.
Why trust BPM.NCRYPT?
Security and the encryption of programmable devices to protect intellectual property and the products in which these devices are used has never been more important than it is today. In fact, customers have been trusting BPWin, BPM’s award-winning Process Software, to provide robust, innovative security solutions for over twenty years.
BPM.NCRYPT leverages our 36 years supporting mission critical devices along with our proven experience developing and releasing sophisticated security and encryption solutions that meet your unique needs. All of our automated machines are enabled to support MES factory integration with BPWin API and include complex security features, at no additional cost. If you are like us, we believe one size or one solution does not fit all. It starts with a conversation– what do you want to accomplish?
Cyber-Security Solutions from BPM
Unlike other security solutions that are expensive, rigid, and one-size-fits-all, BPM offers a range of options based on your particular needs
- BPM.NCRYPT is Flexible: It can integrate with your existing security systems
- BPM.NCRYPT is Scalable: we don’t require a separate HSM for each of our automated systems; One HSM (or secure server) can support several BPM high-speed programming systems
- BPM.NCRYPT is Affordable: BPM does not charge per device and all of our APS are enabled to support encryption; you have an initial investment with no usage fees
Flexible, Scalable, Affordable
BPM.NCRYPT can utilize your existing HSM, secure server, or many other networked and offline data sources. BPM Microsystems can also provide a turn-key package.
Why trust BPM.NCRYPT?
Security and the encryption of programmable devices to protect intellectual property and the products in which these devices are used has never been more important than it is today. In fact, customers have been trusting BPWin, BPM’s award-winning Process Software, to provide robust, innovative security solutions for over twenty years.
BPM.NCRYPT leverages our 36 years supporting mission-critical devices along with our proven experience developing and releasing sophisticated security and encryption solutions that meet your unique needs. All of our automated machines are enabled to support MES factory integration with BPWin API and include complex security features, at no additional cost. If you are like us, we believe one size or one solution does not fit all. It starts with a conversation– What do you want to accomplish?
The following two use cases exemplify what is possible with a combination of proven BPWin features and some customization to support the unique requirements of the project.
Case 1:
Hardware Security Module (HSM) Key Pair Generation and Programming using BPM.NCRYPT
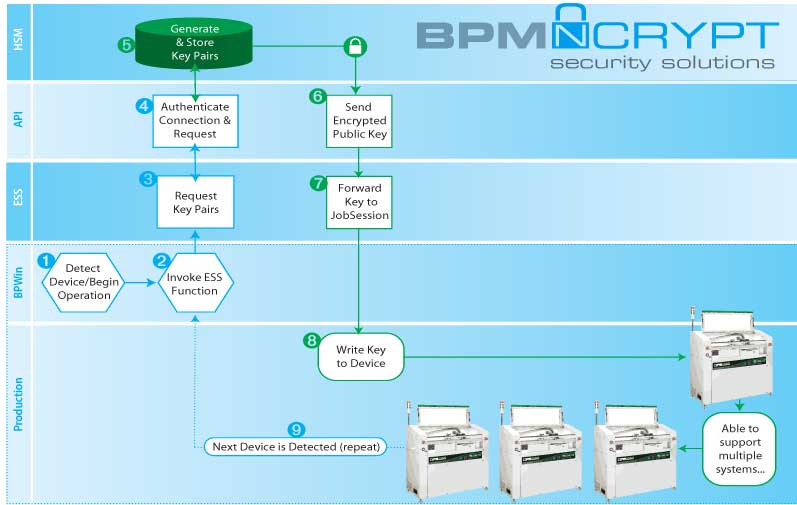
A remote or local HSM is used to program encrypted keys into production devices in real-time. BPWin leverages the External Serialization Server feature, “ESS,” to communicate to the HSM through an API authentication process. During this process, Key Pairs are generated and stored in the HSM, while the encrypted public key is provided as needed by the programming job session. BPWin forwards the specific device data to the device, along with the data pattern stored in the site’s memory. Public Keys are programmed, but not retained by the programming system. All of this is accomplished at the speed of electrons. With modern high-speed HSM technology, multiple factories and machines can be supported.
- Job starts and the Programmer detects a blank device in the socket
- BPWin invokes the ESS function
- ESS requests key pair generation
- API authenticates via a secure connection to the HSM, requests Key Pair from the HSM
- HSM validates the API request and generates the Key Pair
- The API receives the encrypted public key from HSM and passes it to the ESS
- Encrypted Public Key is collected and forwarded to BPWin
- BPWin programs the general data pattern for the job and then writes the unique public key to the Device Under Test (DUT). Important: The public key is erased from the programming site memory, not retained.
- The next blank device is detected; repeating the process starting at Step 2
HSM servers are a popular option for generating secure Key Pairs but are not the only option available for encryption and serialization supported by BPM.NCRYPT.
Case 2:
Certificate Generation with Factory Authentication using BPM.NCRPYT
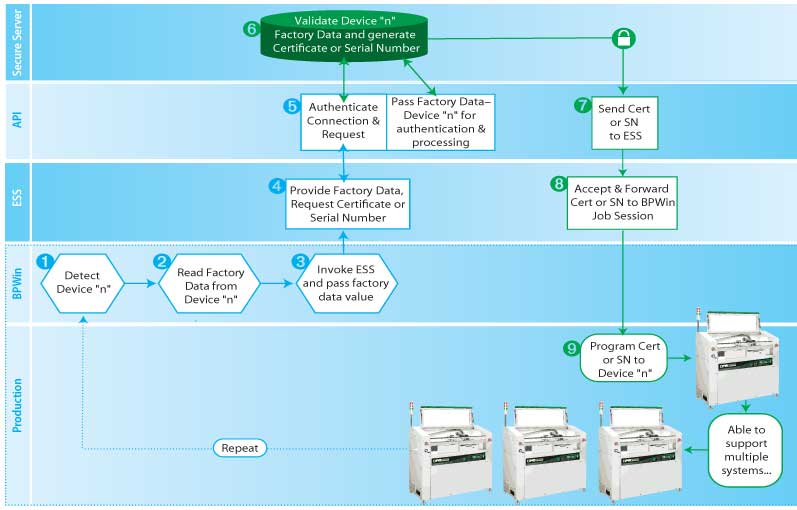
There are a number of options available for generating device certificates or serial numbers; some are as simple as a pre-built database table or randomized data. In some cases, the security process begins with authenticating the device that is being programmed by communicating with a remote factory server. Programmable devices are often shipped with factory programmed content. Using BPM.NCRYPT, factory data in each device is read and sent to a remote factory server for validation. If the data confirms the device is valid, a certificate of authentication is generated and returned to the BPWin programming job session. Each device is thus authenticated, and the electronic certificate is programmed along with the general data pattern. This process creates a unique electronic identity for the device and the end-product in which it will be used.
- Job starts and the Programmer detects a blank device in the socket
- The factory preprogrammed content is Read from the device
- BPWin invokes the ESS function and provides the data read from the device
- ESS requests a validation certificate or serial number
- API authenticates via a secure connection to the factory Server
- The factory data previously read from the device is passed to the server for authentication
- After authentication, the server generates a Certificate (or serial number) that is passed back to the API
- The API receives the certificate (typically encrypted) and passes it to the ESS
- BPWin programs the general data pattern for the job and then writes the certificate or serial number to the Device Under Test (DUT). Important: The certificate is erased from the programming site memory after each iteration.
- The next blank device is detected and the process is repeated until the job is complete.
It’s important to note that the entire authentication process can take place in milliseconds, not slowing the programming session. Modern servers are well equipped to serve multiple BPM.NCRYPT calls in parallel.
BPM.NCRYPT is flexible, scalable and affordable

Flexible
It can integrate with your existing security systems. Can be customized to the unique requirements of the project
Collaborative Solutions
Specific project specifications can be developed collaboratively with customers and we can leverage the many years of experience our team has delivering robust security solutions
Capable on All APS Platforms
All of our automated programming systems are shipped fully enabled to support security, encryption, authentication and sequential or complex serialization within the programming process
