by Colin Harper | Feb 28, 2024 | Cybersecurity, News
In the age of interconnected devices, the significance of cybersecurity within the Internet of Things (IoT) ecosystem has never been more paramount. As these devices permeate every aspect of our lives—from healthcare to automotive, home automation to industrial control systems—their security implications scale correspondingly. The exponential growth of IoT devices has brought forth not only convenience and efficiency but also a myriad of security challenges, making it crucial for stakeholders to prioritize robust security measures to protect sensitive data and maintain device integrity.
The regulatory landscape for IoT security is rapidly evolving, with jurisdictions around the world establishing frameworks to safeguard these technologies. The European Union’s Cybersecurity Act and the United States’ IoT Cybersecurity Improvement Act of 2020 exemplify legislative efforts aimed at setting a baseline for cybersecurity practices. These regulations not only mandate security standards but also encourage manufacturers and developers to adopt security-by-design principles, ensuring that devices are secure from the outset.
In the EU, the General Data Protection Regulation (GDPR) that became effective on May 25, 2018, focuses on data privacy, which impacts IoT devices that collect personal data. The EU Cybersecurity Act, effective June 27, 2019, strengthens the EU’s cybersecurity framework by establishing a certification framework for ICT products, services, and processes, including IoT devices. Furthermore, the EU introduced the NIS Directive 2, requiring EU countries to pass laws by October 2024 to enhance national cybersecurity. The Cyber Resilience Act, proposed in 2022 and expected to be formally approved in 2024, introduces specific obligations for products with digital elements, aiming to embed cybersecurity throughout their lifecycle.
The Cyber Resilience Act is particularly noteworthy as it represents the first EU-wide legislation to impose cybersecurity rules on IoT manufacturers and developers. This legislation requires IoT device makers to inform authorities and consumers about attacks and mandates quick fixes to problems. Moreover, it establishes significant penalties for non-compliance, up to €15 million or 2.5% of the previous year’s global turnover, and gives the EU powers to recall and ban non-compliant products. The Act emphasizes the importance of security by design, mandating that IoT products meet “essential” cybersecurity requirements before they can go to market. Manufacturers will need to start incorporating security at the design stage to ensure that devices are compliant with the upcoming regulations.
In the US, the landscape is more fragmented, with no comprehensive federal law specifically targeting IoT security. However, the IoT Cybersecurity Improvement Act of 2020, signed into law on December 4, 2020, represents a significant step toward regulating IoT security at the federal level. This law mandates the National Institute of Standards and Technology (NIST) to develop and manage IoT cybersecurity standards for federal government devices. Additionally, California has taken a proactive stance with its own IoT cybersecurity law, SB-327, effective January 1, 2020, which requires manufacturers of connected devices to equip them with reasonable security features.
These regulatory efforts in the EU and US illustrate a growing recognition of the need for robust cybersecurity measures to protect the increasing number of connected devices. The emphasis on security by design and the requirement for manufacturers to be more transparent about the cybersecurity of their devices are critical steps towards ensuring that IoT devices are secure from their inception and throughout their lifecycle.
BPM Microsystems emerges as a leader in this challenging environment, with its pioneering role in device programming emphasizing its commitment to security and innovation. Specializing in the development of programming technologies for microcontrollers, flash memories, and other components, BPM Microsystems understands the criticality of secure device programming in the IoT ecosystem. Its solutions are designed to cater to the pressing need for secure programming practices, ensuring that devices are safeguarded against unauthorized access and tampering from the manufacturing stage.
A testament to BPM Microsystems’ dedication to cybersecurity is BPM.NCRYPT, a feature that underscores the company’s comprehensive approach to encryption and secure programming. BPM.NCRYPT provides an extra layer of security by ensuring that data remains encrypted throughout the programming process, minimizing the risk of interception or tampering. This feature is integral to BPM Microsystems’ efforts to meet and exceed the security requirements in device programming, offering manufacturers a reliable solution for securing their devices.
The BPWin software further amplifies BPM Microsystems’ commitment to security through its support for encryption. For years, BPWin has facilitated secure programming processes, enabling manufacturers to program devices with the assurance that their data is protected. This software is pivotal in enhancing the security of device programming operations, underscoring BPM Microsystems’ role in addressing the evolving cyber threats facing the IoT landscape.
BPM Microsystems’ adoption of the security-by-design principle is emblematic of its proactive approach to cybersecurity. By integrating security features early in the device development cycle, the company ensures that its products are not only compliant with current standards but also equipped to mitigate future risks effectively. This principle is fundamental to developing secure, reliable IoT devices that can withstand the complexities of the modern cyber environment. By adhering to these guidelines, BPM Microsystems not only reinforces its position as a thought leader in secure device programming but also contributes to the overall safety and reliability of IoT technologies.
Looking ahead, the challenges in IoT security are set to grow in complexity and scale. However, BPM Microsystems is well-positioned to address these challenges through continuous innovation and adherence to best practices in cybersecurity. The company’s commitment to developing secure programming solutions is vital to the future of IoT security, ensuring that devices remain protected against an ever-evolving landscape of cyber threats.
In conclusion, the imperative for secure device programming in safeguarding IoT devices cannot be overstated. As regulations within the IoT landscape continue to expand, the role of industry leaders like BPM Microsystems in navigating the complexities of IoT security becomes increasingly critical. Through its pioneering solutions and commitment to cybersecurity, BPM Microsystems exemplifies the importance of a proactive and comprehensive approach to securing IoT devices. Stakeholders across the IoT spectrum would do well to recognize the value of partnering with companies that prioritize security, ensuring a safer and more secure future for IoT technologies.

by Scott Bronstad | Jan 26, 2023 | Cybersecurity, How To, Technology
Cybersecurity is a critical concern to secure data for offline device programming, as it ensures the integrity and confidentiality of the programming process. Below are several ways to implement cybersecurity in device programming, with tips on what you should be doing today, including access control, encryption, software updates, risk assessment/management, audits, and education.
Access control
Implementing strict access controls can prevent unauthorized access to the programming equipment and software. This can include physical security measures to secure data, such as security cameras and access cards, as well as software-based security measures, such as password protection and multi-factor authentication.
- Use security cameras to monitor access to the programming equipment and software.
- Use access cards or biometric authentication to control access to the programming equipment and software.
- Implement software-based security measures, such as password protection and multi-factor authentication.
- Regularly review and update access controls to ensure they are still effective.
- If possible, remove outside access to networks and the internet. No access makes it almost impossible to hack.
- Deeper dive here
Secure Data with Encryption
 Encrypting the programming data and communication between the programming equipment and software can secure data against data breaches and unauthorized access to the programming data.
Encrypting the programming data and communication between the programming equipment and software can secure data against data breaches and unauthorized access to the programming data.
- Use strong encryption algorithms to protect the programming data.
- Implement key management to ensure that only authorized personnel have access to the encryption keys.
- Regularly review and update encryption methods to ensure they are still effective.
- 9 best encryption software programs for 2023
Secure software updates
Regularly updating the programming equipment and software is important for keeping them secure. However, it’s important to ensure that these updates are coming from a trusted source and are properly authenticated before installation.
- Ensure that updates are coming from a trusted source and are properly authenticated before installation.
- Keep track of software version and updates history.
- Verify the authenticity of software updates and the update process.
Risk assessment and management
Conducting regular risk assessments and implementing a risk management plan can help identify and mitigate potential vulnerabilities in the programming process.
- Implement a risk management plan to mitigate identified vulnerabilities.
- Evaluate the effectiveness of the risk management plan and update it as needed.
- Deeper dive here
Regular security audits
Regularly auditing the programming process and equipment can help identify and address any security weaknesses. Treat cyber threats as you would an ISO audit.
- Use both automated and manual testing methods.
- Use third-party security experts to conduct regular security audits.
- Keep records of security audits and implement recommendations.
Employee education and awareness
Educating employees about the importance of cybersecurity and how to properly handle and protect programming equipment and data can help prevent human error-based security breaches.
- Provide regular cybersecurity training to employees.
- Create and implement security guidelines and policies.
- Encourage employees to report any suspicious activities or security breaches.
- Run regular cybersecurity drills and simulations.
Implementing these security measures can help ensure the integrity and confidentiality of the offline semiconductor device programming process and protect against potential cyber threats. While this article focuses on offline programming, many of these principles apply to other types of device programming as well. In short, it’s important to regularly review and update these security measures to ensure they stay effective in protecting against evolving cyber threats.
Learn More
by Scott Bronstad | Jan 25, 2023 | Cybersecurity, Technology
As technology continues to advance and evolve, the use of semiconductor devices has become increasingly prevalent in a variety of industries, including telecommunications, computing, and even healthcare. While these devices offer numerous benefits and capabilities, their programming and use also raise important ethical considerations.
Potential for Abuse
One significant ethical consideration related to semiconductor device programming is the potential for abuse of the devices. For example, in the realm of computing, programming a semiconductor device to hack into a computer system or access sensitive information without permission is clearly unethical. Similarly, programming a semiconductor device to facilitate identity theft or other forms of fraud is also unethical.
Hacking and Cybersecurity
Another ethical consideration related to device programming is the potential for malicious actors to exploit vulnerabilities in these devices to cause harm. For example, if a semiconductor device used in a critical infrastructure system, such as a power grid or water treatment plant, is vulnerable to hacking, it could potentially be manipulated to cause widespread disruption or damage; or programming a device used in a medical device to malfunction or deliver incorrect treatment could have serious consequences for the patient. Similarly, programming a semiconductor device used in transportation systems (such as self-driving cars) to malfunction could lead to accidents and harm to both passengers and bystanders.
Additionally, programming errors or vulnerabilities in semiconductor devices used in personal devices, such as smartphones or laptops, could leave individuals vulnerable to cyber-attacks such as data breaches or theft of personal information. It is important for manufacturers, developers, and operators to ensure that these devices are properly secured and tested for vulnerabilities to minimize these risks, and to have a plan in place to mitigate the damage of a successful attack.
Bias
A third ethical consideration related to semiconductor device programming is the potential for discrimination or bias. For example, programming a semiconductor device used in hiring or promotion decisions to favor certain groups or individuals based on characteristics such as race or gender could be considered unethical. Similarly, programming a semiconductor device used in credit or loan decisions to unfairly disadvantage certain groups or individuals could also be considered unethical.
Skynet
Certainly, one ethical consideration related to semiconductor device programming, albeit perhaps more far-fetched, is the potential for the development of artificial intelligence (AI) systems that are capable of autonomous decision-making. This is similar to the concept of Skynet, a fictional AI system in the Terminator franchise that becomes self-aware and turns against humanity. As the capabilities of semiconductor devices and AI systems continue to advance, it is important to consider the potential consequences and ensure proper safety measures and regulations are in place to prevent negative outcomes.
In order to address these ethical considerations, it is important for those involved in semiconductor device programming to consider the potential consequences of their actions and to ensure that their programming is ethical and responsible. This may involve implementing safeguards and controls to prevent abuse or misuse of the devices, as well as regularly reviewing and evaluating the programming to ensure that it is not causing harm or discrimination.
Ultimately, the ethical considerations of device programming highlight the need for ongoing dialogue and discussion about the responsible use of technology. By considering the potential consequences of our actions and making ethical choices, we can ensure that the benefits of semiconductor devices are maximized while minimizing any negative impacts.
Learn More
by Scott Bronstad | Dec 21, 2022 | Cybersecurity
Benefits of Cybersecurity
Implementing robust manufacturer cybersecurity measures can provide several benefits for manufacturers. Some of these benefits include:
- Protecting sensitive information: Cybersecurity measures can help protect sensitive information, such as trade secrets, intellectual property, and customer data, from being accessed or stolen by unauthorized individuals or organizations. Modern manufacturers often handle sensitive information such as intellectual property, trade secrets, and customer data. Cybersecurity measures can help protect this information from being accessed by unauthorized individuals or organizations.
- Maintaining customer trust: A breach of cybersecurity can lead to the loss of consumer trust and damage to a company’s reputation. End users expect their personal and financial information to be protected when doing business with a manufacturer. By implementing strong cybersecurity measures, manufacturers can maintain customer trust and reduce the risk of damaging their reputations.
- Meeting regulatory requirements: Many industries have specific cybersecurity regulations that must be met. By implementing robust cybersecurity measures, manufacturers can ensure compliance with these regulations and avoid potential fines or other consequences.
- Avoiding financial losses: Cyberattacks can result in significant financial losses for manufacturers. These losses can come from the cost of responding to the attack, as well as lost revenue and profits due to disrupted operations. Implementing robust cybersecurity measures can help prevent these losses.
- Ensuring operational continuity: Cyberattacks can disrupt manufacturing operations, leading to delays and other issues. By implementing robust cybersecurity measures, manufacturers can ensure that their operations continue smoothly and without interruption.
- Improving operational efficiency: Cybersecurity breaches can disrupt manufacturing operations, leading to lost productivity and revenue. Implementing robust cybersecurity measures can help prevent these disruptions and improve operational efficiency.
- Reducing financial risk: Cybersecurity breaches can result in significant financial losses, including the cost of responding to the breach, damages to reputation, and legal fees. Implementing strong cybersecurity measures can help reduce the risk of these financial losses.
Implementing Manufacturer Cybersecurity
- Conduct a cybersecurity risk assessment to identify vulnerabilities and potential threats to your manufacturing operations. This should include evaluating the security of your network infrastructure, identifying any weak passwords or lack of multi-factor authentication, and assessing the security of your connected devices and systems.
- Implement strong password policies and ensure that all employees are using unique, complex passwords for all accounts and systems. Consider implementing multi-factor authentication for added security.
- Regularly update and patch all software and systems to ensure that any known vulnerabilities are addressed.
- Implement network segmentation to limit the spread of any potential cyber threats and isolate sensitive data from non-sensitive areas.
- Implement a firewall and intrusion detection/prevention systems to monitor and protect against potential cyber threats.
- Regularly train employees on cybersecurity best practices and make sure they are aware of the potential risks and how to identify and report potential threats.
- Implement a security incident response plan to have a clear process in place for handling any potential cyber threats.
Many BPM users operate in a strict no-internet connection environment. This is a crude yet highly effective security measure.
Due to the rapid changes in threats and the general ignorance of best practices, you should seriously consider working with a cybersecurity expert or consulting firm to ensure that your manufacturing operations are adequately protected.
Manufacturer Cybersecurity Solutions from BPM
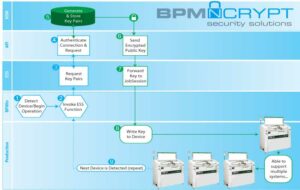 Unlike other security solutions that are expensive, rigid, and one-size-fits-all, BPM offers a range of options based on your particular needs
Unlike other security solutions that are expensive, rigid, and one-size-fits-all, BPM offers a range of options based on your particular needs
- Flexible: It can integrate with your existing security systems. Can be customized to the unique requirements of the project
- Scalable: we don’t require a separate HSM for each of our automated systems; One HSM (or secure server) can support several BPM high-speed programming systems
- Affordable: BPM does not charge per device and all of our APS is enabled to support encryption; you have an initial investment with no usage fees
Cybersecurity Solutions from BPM | Easy Engineering Interview



 Unlike other security solutions that are expensive, rigid, and one-size-fits-all, BPM offers a range of options based on your particular needs
Unlike other security solutions that are expensive, rigid, and one-size-fits-all, BPM offers a range of options based on your particular needs