Benefits of Cybersecurity
Implementing robust manufacturer cybersecurity measures can provide several benefits for manufacturers. Some of these benefits include:
- Protecting sensitive information: Cybersecurity measures can help protect sensitive information, such as trade secrets, intellectual property, and customer data, from being accessed or stolen by unauthorized individuals or organizations. Modern manufacturers often handle sensitive information such as intellectual property, trade secrets, and customer data. Cybersecurity measures can help protect this information from being accessed by unauthorized individuals or organizations.
- Maintaining customer trust: A breach of cybersecurity can lead to the loss of consumer trust and damage to a company’s reputation. End users expect their personal and financial information to be protected when doing business with a manufacturer. By implementing strong cybersecurity measures, manufacturers can maintain customer trust and reduce the risk of damaging their reputations.
- Meeting regulatory requirements: Many industries have specific cybersecurity regulations that must be met. By implementing robust cybersecurity measures, manufacturers can ensure compliance with these regulations and avoid potential fines or other consequences.
- Avoiding financial losses: Cyberattacks can result in significant financial losses for manufacturers. These losses can come from the cost of responding to the attack, as well as lost revenue and profits due to disrupted operations. Implementing robust cybersecurity measures can help prevent these losses.
- Ensuring operational continuity: Cyberattacks can disrupt manufacturing operations, leading to delays and other issues. By implementing robust cybersecurity measures, manufacturers can ensure that their operations continue smoothly and without interruption.
- Improving operational efficiency: Cybersecurity breaches can disrupt manufacturing operations, leading to lost productivity and revenue. Implementing robust cybersecurity measures can help prevent these disruptions and improve operational efficiency.
- Reducing financial risk: Cybersecurity breaches can result in significant financial losses, including the cost of responding to the breach, damages to reputation, and legal fees. Implementing strong cybersecurity measures can help reduce the risk of these financial losses.
Implementing Manufacturer Cybersecurity
- Conduct a cybersecurity risk assessment to identify vulnerabilities and potential threats to your manufacturing operations. This should include evaluating the security of your network infrastructure, identifying any weak passwords or lack of multi-factor authentication, and assessing the security of your connected devices and systems.
- Implement strong password policies and ensure that all employees are using unique, complex passwords for all accounts and systems. Consider implementing multi-factor authentication for added security.
- Regularly update and patch all software and systems to ensure that any known vulnerabilities are addressed.
- Implement network segmentation to limit the spread of any potential cyber threats and isolate sensitive data from non-sensitive areas.
- Implement a firewall and intrusion detection/prevention systems to monitor and protect against potential cyber threats.
- Regularly train employees on cybersecurity best practices and make sure they are aware of the potential risks and how to identify and report potential threats.
- Implement a security incident response plan to have a clear process in place for handling any potential cyber threats.
Many BPM users operate in a strict no-internet connection environment. This is a crude yet highly effective security measure.
Due to the rapid changes in threats and the general ignorance of best practices, you should seriously consider working with a cybersecurity expert or consulting firm to ensure that your manufacturing operations are adequately protected.
Manufacturer Cybersecurity Solutions from BPM
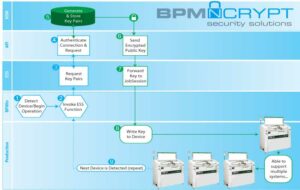 Unlike other security solutions that are expensive, rigid, and one-size-fits-all, BPM offers a range of options based on your particular needs
Unlike other security solutions that are expensive, rigid, and one-size-fits-all, BPM offers a range of options based on your particular needs
- Flexible: It can integrate with your existing security systems. Can be customized to the unique requirements of the project
- Scalable: we don’t require a separate HSM for each of our automated systems; One HSM (or secure server) can support several BPM high-speed programming systems
- Affordable: BPM does not charge per device and all of our APS is enabled to support encryption; you have an initial investment with no usage fees
Cybersecurity Solutions from BPM | Easy Engineering Interview